
At Emproof, our mission is to enhance the security and integrity of embedded systems through innovative binary rewriting techniques. We are committed to providing advanced […]
June 26, 2024

The notion that reverse engineering is exclusive to expert hackers is swiftly evolving. Thanks to sophisticated open-source tools such as Ghidra [7], the threshold skills […]
March 4, 2024

This article is a repost. It was originally published at Tim Blazytko’s personal blog: https://synthesis.to/2023/08/02/api_functions.html. During my presentation “Unveiling Secrets in Binaries using Code Detection Strategies” at REcon […]
August 11, 2023

Although memory corruption vulnerabilities have been extensively studied, effective mitigation strategies are still not universally available, particularly in deeply embedded systems with constrained hardware resources, […]
July 17, 2023
Embedded system security is essential and, at the same time, complex and challenging to implement. We deliver high levels of security and IP integrity for embedded systems.
December 17, 2022
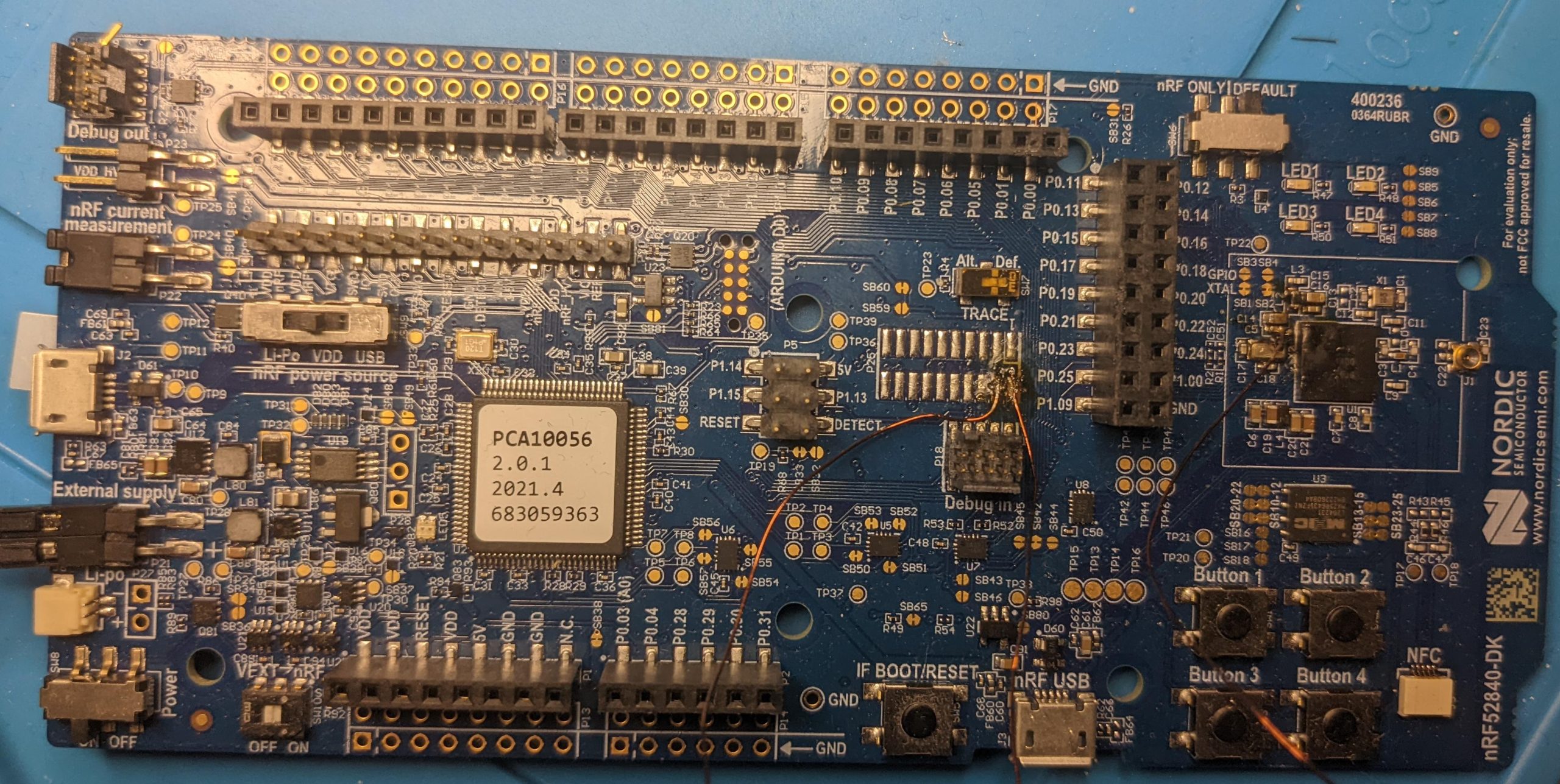
Most modern microcontrollers take measures to protect the contained software. As we have shown previously these protections are not perfect and can be bypassed.
June 10, 2022
In this article, we take a look at some generic heuristics that allow us to quickly identify interesting code parts, and how they work on (partially) obfuscated binaries.
August 10, 2021
Most modern microntrollers allow customers to protect their valuable code and data against unauthorised access using Readout Protection (ROP). This article details how it is possible to acquire the protected firmware from a properly configured device, and unlock all debugging features of the controller.
June 18, 2021
This article illustrates the theory of control-flow graph construction, dominance relations and loop analysis.
March 15, 2021
Commercial businesses and malware authors often use code obfuscation to protect specific code areas to impede reverse engineering. Knowing which code areas are obfuscated often pinpoints sensitive code parts that are worth a closer look.
March 3, 2021




